 Recently, the Microsoft Security Essentials (MSE) running on my Windows 7 64bit desktop detected the “win64/Sirefef.W” virus. The “win64/Sirefef.W” (or variants like “win64/Sirefef.Y” and “win64/Sirefef.B”) is a trojan which can install rootkits and other malicious programs onto your machine, in addition to providing security backdoors and other nasty stuff. On my machine, the “Windows/System32/services.exe” file was infected which is really bad because services.exe is used to launch essential Windows Services.
Recently, the Microsoft Security Essentials (MSE) running on my Windows 7 64bit desktop detected the “win64/Sirefef.W” virus. The “win64/Sirefef.W” (or variants like “win64/Sirefef.Y” and “win64/Sirefef.B”) is a trojan which can install rootkits and other malicious programs onto your machine, in addition to providing security backdoors and other nasty stuff. On my machine, the “Windows/System32/services.exe” file was infected which is really bad because services.exe is used to launch essential Windows Services.
Unfortunately, MSE was unable to clean the “win64/Sirefef.W” virus after detecting it. In the middle of cleaning, the desktop rebooted. On restart, MSE detected the virus again and display a message saying that the machine needed to be rebooted in a minute. A minute later, the desktop rebooted, MSE once again detected the virus and displayed a reboot warning. This cycle looked to repeat endlessly, rendering my Windows 7 64bit desktop useless.
Manual intervention was necessary. Fortunately, I was able to dual-boot the infected desktop to run an older, clean Windows XP operating system. (If you don’t have a dual-boot, see comments for alternative methods to get a clean “services.exe” on your machine; search for JAKiii who updated Andre’s instructions.) More fortunate, I had a clean Windows 7 64bit operating system on my laptop. Using Windows XP, I was able to copy the clean “Windows/System32/services.exe” file from my laptop to the Windows 7 partition on my desktop (I left the corresponding “services.msc” alone). (Note: In the future, if I only had one machine, I would consider having a dual-boot of two Windows 7 operating systems; the first of which is for my day-to-day usage, and the second is a barebones install which is the reference install. I might considering ghosting just the barebone one for easy restore.)
After replacing “services.exe”, I was able to restart my Windows 7 64bit desktop without MSE detecting the virus and forcing a reboot. I then did a full scan with both MSE and Malwarebytes to ensure that the whole machine was clean. I thought the problem was solved, but “win64/Sirefef.W” had damaged Windows 7 by removing security-related Windows services.
I found that the Base Filtering Engine (BFE), Windows Firewall (MpsSvc), Windows Security Center (WscSvc), Windows Update (wuauserv), and Background Intelligent Transfer Service (BITS) services were missing. The “win64/Sirefef.W” virus had deleted their registry entries. To recover, I exported the following registry entries from my laptop and then imported them into my desktop:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\BFE (Base Filtering Engine)
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\MpsSvc (Windows Firewall)
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess (Required by Windows Firewall)
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\WscSvc (Windows Security Center)
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\wuauserv(Windows Update)
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\BITS (Background Intelligent Transfer Service – required by Windows Update)
For your convenience, here is a zip file, SirefefMissingServicesRegistryFix.zip, containing the registry exports above and the clean “\Windows\System32\services.exe” file from my Windows 7 64bit Service Pack 1 (SP1) laptop. The registry exports have file extension “.reg” and you can import the services you are missing by double-clicking on them. (For those who don’t have SP1, John in comments provides a link to his services.exe for Windows 7 Home Premium in addition to instructions on how to extract a version from your Windows 7 install DVD. Please make sure to scan the file with your virus scanner before using. That advice applies to everything, including the zip file that I include above.)
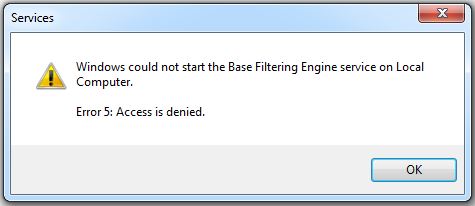
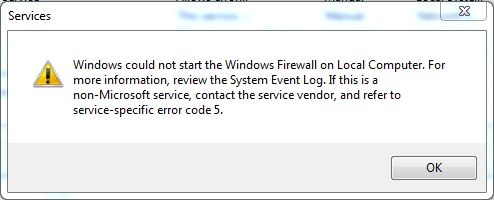
There is an additional step to do below but at this point, we need to reboot once so that the registry changes can take effect and Windows will recognize the “new” services. On reboot, Windows will fail to start the Base Filtering Engine and Windows Firewall services. If you attempt to manually start them, you will encounter “error code 5” messages (see below), which are “access denied” errors. The fix for these access denied errors is to add the necessary permissions to the registry for each of the services. (You can try to avoid this reboot, but Windows may complain if you attempt to add permissions for services like BFE which it may not recognize without a reboot. In this case, just reboot and then repeat the add permission instructions.)
Update: Originally, I couldn’t set an NT service name as a user in the registry permissions so I suggested using the “Everyone” user with “Full Control” permission. While that worked, it left a big security hole. Fortunately, gvozden in the comments provided the solution. I have updated the instructions to replicate the original registry permissions exactly (as set on my laptop).
Do the following to add the necessary registry permissions:
- Run “regedit”.
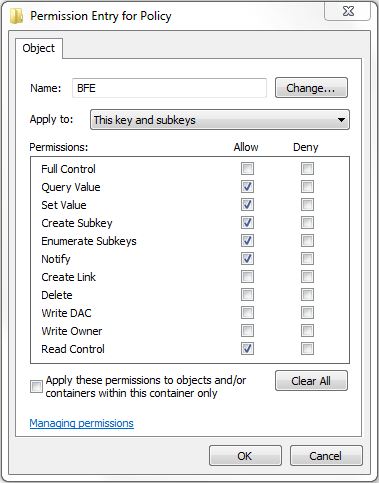
- Browse to the “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\BFE\Parameters\Policy” section.
- Right-click on “Policy” and select “Permissions…”. If you see a “BFE” user listed under the “Group or user names” list, you do not need to add it below.
- Click the Add button, type “NT service\BFE” (it’s actually case-insensitive), and click the OK button.
- Click the Advanced button, double-click on BFE to edit, and select the following in the allow permissions column: Query Value, Set Value, Create Subkey, Enumerate Subkeys, Notify, and Read Control.
- Click OK, OK, and OK to close the Permissions dialog.
- Browse to the “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess” section.
- Right-click on “Epoch” and select “Permissions…”. If you see “MpsSvc” listed, you do not need to add it below.
- Click the Add button, type “NT Service\MpsSvc”, and click the OK button.
- Click the Advanced button, double-click on MpsSvc to edit, and select the following in the allow permissions column: Query Value and Set Value.
- Click OK, OK, and OK to close the Permissions dialog.
- Repeat the steps above for “Epoch2”.
- (Note: I could run the Windows Firewall without permissions set on the following two registry keys; but on my laptop, they were set so I also set them on the desktop just in case.)
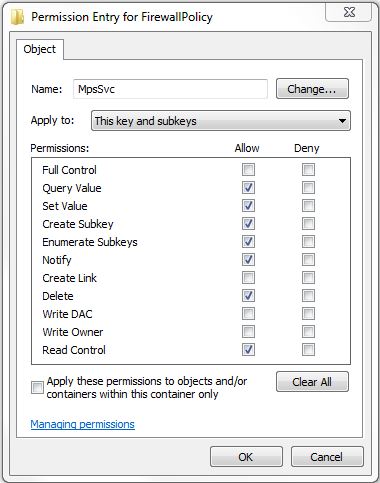
- Browse to the “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess\Defaults\FirewallPolicy” section.
- Right-click on “FirewallPolicy” and select “Permissions…”. If you see “MpsSvc” listed, you do not need to add it below.
- Click the Add button, type “NT Service\MpsSvc”, and click the OK button.
- Click the Advanced button, double-click on MpsSvc to edit, and select the following in the allow permissions column: Query Value, Set Value, Create Subkey, Enumerate Subkeys, Notify, Delete, and Read Control.
- Click OK, OK, and OK to close the Permissions dialog.
- Repeat the above for the “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy” section.
- Reboot the machine.
- After the reboot, run “services.msc” and check that the “Base Filtering Engine”, “Windows Firewall”, “Security Center”, “Background Intelligent Transfer Service”, and “Windows Update” services are started successfully. The last three services are set to delayed start so they may not have started yet; in this case, you can manually start them.
- Run “Check security status” to see what Windows thinks about the security of the machine.
- Run “Windows Update” to get the latest security updates from Microsoft.
Note: The “Base Filtering Engine” depends on the “IPsec Policy Agent” and “IKE and AuthIP IPsec Keying Modules” services. Thankfully, the “win64/Sirefef.W” virus left these two services alone on my desktop.
If you prefer the command line, you can use the Service Control Manager “\Windows\System32\sc.exe” command line program instead of the “services.msc” program. Just run the “Command Prompt” as an administrator and input “sc” to see the command line options. Some useful ones I found were:
- “sc qdescription wcssvc” which returns the human-friendly name “Windows Security Center” for “wcssvc”.
- “sc query mpssvc” which returns the status for the “Windows Firewall” including recent exit codes.
- “sc start bfe” which will attempt to start the “Base Filtering Engine” service.
I found the following websites helpful while researching this topic:

Great job Chanh. I don’t see the attachement to the clean services.exe though???
Thanks. I modified the post to make the link to the zip file more explicit. Just search for “SirefefMissingServicesRegistryFix.zip” and click on it to download the zip file. The clean services.exe file is inside the zip file.
Brilliant article exactly replicated and fixed my problem, thanks fo your help
This was a fantastic article!! Very well done. Bit of work ahead for anyone tackling this…but THIS article is the answer!! Thanks, Trevor
It was my Windows 64-bit Home Premium laptop that got nailed. Ouch.
Brilliant Article, I have been struggling with this for a couple of days. Thanks so so so much !!!
Here is something I found that may help others. Feel free to add to article if this helps.
I only had one machine, so I was worried how I was going to replace the service.exe
In the end I did the following.
1) I went into msconfig and I selected boot without services. (I don’t know if this is important or not, I just had it like this so I wanted to mention it)
2) I downloaded the file above.
3) In taskmanager I killed the “services.exe” process. Note you have to enable “show processes from all users” to see the “services.exe” process. At this point you get a “critical error, reboot in 1 min message”.
4) I immediately pasted the clean services.exe over the infected one to replace it before reboot.
5) Now complete the rest of the article above.
Hope it helps
Cheers
Andre
Thanks, Andre. I added a sentence for folks to check the comments for alternative methods if they didn’t have a dual boot available.
thanks for the instructions! I put the services.exe on a usb key, CD booted with Winternals 2007 and replaced the file. This stopped the rebooting cycle. Then I ran ComboFix.exe in windows. After that finished I ran GMER, Malwarebytes and MSE and they all come up negative for the infection.
Very nice work, but Everyone:Full on the services is a bit sloppy.
Here’s how to add the correct permissions on BFE and MpsSvc:
HKLM\SYSTEM\CurrentControlSet\Services\BFE edit permissions to include entity “NT Service\bfe” (verifes as BFE) and provide full control.
HKLM\SYSTEM\CurrentControlSet\Services\MpsSvc edit permissions to include entity “NT Service\mpssvc” (verifies as MpsSvc) and provide full control.
Thanks, gvozden! I’ve updated the post with your instructions.
thanks for the article, but I still need some help: so I log on to my account, I turn on the task manager and click “show processes from all users”, which is an administrator button, I spotted the services.exe and ended the process, but that accelerates the appearance of that reboot msg…I am not sure how exactly to beat the speed of that virus’s appearance, is there other ways of replacing a new services.exe?
BTW, I also run Windows 7 64bit
Vigilant111, thanks for the comment. There are several options that comes to mind concerning booting your machine from a CD/DVD or USB drive.
1) From the comments, it sounds like Mike Tech was able to use a Winternals 2007 bootable CD.
2) If you have a friend with Windows 7 64bit, you can ask the friend to create a recovery CD/DVD. See section “How to: Windows 7 Recovery Disk/Bootdisk” under BootDisk.info. This website may also suggest other alternatives.
3) I believe that Windows XP is mostly compatible with Windows 7 NTFS so if you have a bootable Windows XP CD, that should work also. In the past, I created such a bootable CD using BartPE. See section “Create a BartPE bootable Windows XP CD…” in my previous post Replace the System Drive With a Larger Hard Drive for details.
Unfortunately, all the above pre-supposes that you have a bootable CD/DVD or a working computer to create such. Hope that it helps.
Thank you so much for sharing this information! This was the only article that solved the problem on my system.
Thanks for all your instructions to get rid of this problem, but I seem to be stuck on step 2 in the registry permissions. When I try to add NT service\bfe I get the message that “An object named “nt service \bfe” cannot be found. I can’t figure out whats going wrong. I’ve double checked that I’ve followed the instructions step by step but can’t get any further 🙁
Sorted it now. I rebooted and there it was 🙂 Thank you very, very much again!!! Very much appreciated.
I’ve got the virus on my computer. Believe it came through a rogue antivirus called “Live security Platinum”, which I saw many people infected with this month complaining.
Went through the listed advice to fix.
I believe I killed it.
But…As many have reported online, the services the virus killed are more than the ones listed above (antivirus, firewall, etc…)
On my end, I have problems which I have seen recurring on the internet:
1. Windows Defender also shut down (managed to download regedit key for this and got it back on)
2. Icons on my desktop auto-order alphabetically and will reset so every time I turn on my computer. This is a recurring issue for many people.
3. Got a message on the bottom right saying my Battery needs replacement. It popped up when the virus attacked and I suspect it’s fake.
My question :
Anybody know how to fix these issues with (I suspect), REGEDIT ?
Also, How can we basically restore the registry to its full health as I have seriously no idea the extent its been damaged by this virus ?
Thanks so much for your help…
I also got issue #2 where after each restart, the icons on my desktop were totally re-arranged. I tried to fix it using the Regedit (for example: deleting the existing HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bag and BagMRU where custom folder settings are stored) but could not succeed.
I finally solved it by creating a new User and then moving my stuff over to the new user. The newly created user did not have any issues with the desktop icons getting rearranged.
Maybe creating a new user will also fix the false battery replacement warning message? I do know that creating a new user starts you off with a fresh HKEY_CURRENT_USER registry tree.
Alternatively, if you don’t want to re-create the user and are ok with using a free 3rd-party tool to handle the desktop icon arrangements, I recommend the Stardock Free Fences utility. I just started using it and like how it arranges icons into shaded regions on the desktop.
Hi, thanks for the solution. My problem is that when I try to create the user permissions, I only see the users listed under windows such as administrator and me as a user, it does not allow me to add for example “NT service\BFE”. What might be the problem here?
You won’t see “NT service\BFE” or “NT service\MpsSvc” listed under “Available group or user names”. Instead, I just typed the text in the “Enter the object names to select” input box.
I’ve created a new user account and deleted the old one. The problem remains.
Everything I restart the computer the icons move around and this also happens when I right click and refresh.
Anybody know how to fix this, must be a registry problem. I really don’t want to format my PC.
Guys…
Ran Combofix and it fixed the icons problem for me.
Found 1 infected file, I believe kernel within system 32.
Thanks for your help. after replacing services.exe, Im having just some “fun” on regedit permissions.
Thanks Chanh for the quick response. I do have one more problem though, I have noticed that Windows defender is not working. When I try to start it I get an error message “The specified service does not exixt as an installed service. (Error code: 0x8007o424)”
Hi Rodgers. Anon2012 is correct. You will need to get an export of the Windows Defender service registry keys or just re-install Windows Defender to get it working again. Unfortunately, I don’t have Windows Defender so cannot export the registry keys for it. I am using Microsoft Security Essentials which is the replacement for and upgrade of Windows Defender. I believe Microsoft recommends that Windows Defender be uninstalled and replaced with Security Essentials.
@Rodgers
This usually happens with this virus. Happened to me too.
You gotta download the windows defender registry key. Its been wiped out by the virus.
Hi,
thanks for the good article – helps me to clean my PC – I still have only one Problem:
All Networkconnections are not working, all related Services are not running – If I try to start it, I get a Error 5 – seems that some of the permissions or Reg entries are not correct – can you give me any support on this
Thanks
Hi Thomas,
It looks like you have a different, though related issue with Network Connections service not running. I found a great web page on this called Network connections not appearing in network list in Win 7. From that page and other pages, I think here is a possible plan of action, one of which might fix your issue:
Hope that you fix your issue.
Brilliant article, fixed my problem, thank you so much for sharing this information! This was the only article that solved the problem on my system, thanks fo your help.
Thanks for the tips. I used andre’s comment to stop the reboots.. now to rebuild the damage…
Thank you so much for this! I was infected with Win64/Sirefef.B and was able to fix it using your clean services.exe, you’ve saved me a lot of effort!
Thank you for this, it took me like 20 tries to replace the services.exe before it restarted, but I managed to do it in the end.
I’m having some trouble at this step though:
Click the Add button, type “NT service\BFE” (it’s actually case-insensitive), and click the OK button.
When I click OK, another window pops up that says “An object named “NT service\BFE” cannot be found, and what appears to be a prompt to retry, which just keeps returning that same window.
All the boxes are checked in “Select this object type:” and the only location in “From this location:” is my laptop.
I’m too scared to poke around in regedit without any instructions, so any help would be appreciated.
Hi Othelen, my instructions above may be wrong concerning rebooting. You may need to reboot the computer immediately after importing the registry entries for the BFE and other services. After the reboot, when adding the registry permissions, Windows should recognize “NT service\BFE” as a service name. Please let me know if this fixes your issue so that I may update the post accordingly. Thanks.
Well that is it. 12 hours of work and finally got rid of it thanks to this amazing thred. Thanks all. I dont dual boot so I was truing to kill the services.exe or rename to get rid of it but this caused blue screen of death on following reboot. I put my windows 7 disk in and did a repair and restore to previous state. This seemed to do the trick as it stopped rebooting. I then scanned with MSE and malwarebytes and cleared off some 23 occurances and numerous registry entries of the trojan. I may scan with some more antivirus suppliers just to make sure they have all been found.
The restore and repair also cured all my networking and firewall issues.
Thank you, rebooting did the trick.
Thanks for the update, Othelen. I’m glad it worked. I’ve updated the post to request a reboot after importing the service registry files and before attempting to add registry permissions.
Phew! Thank you so much for this — the .zip file and the step-by-step instructions have been fantastically helpful. Much appreciated!!
You, sir, are awesome! Thank You!
Great write up. I tried using the microsoft emergency scanner (“Google” msert.exe) to get rid of the virus and got stuck in the same loop you mentioned at the top of the article. I did not have a clean Win 7 PC or dual boot option so I ran SFC /Scanfile=C:\Windows\System32\Services.exe SFC correctly identified that services.exe was corrupted and needed a reboot to replace it. Upon reboot the cycle was broken but then I started trying to find registry keys I could import, that’s when I found your page. Thanks for putting everything in one place for me!
This Article and the comments saved me. Although I have other PCs in the house, I found it easy to follow Andre’s advice. Here’s what I did:
1. On the infected PC, run msconfig and check the boxes that allow a boot without services
2. Quickly reboot before the system reboots itself
3. Open Task Manager and disable the services process
4. Copy the clean services.exe file into Windows/System32
5. Reboot again before the system reboots itself.
6. Follow the rest of the article’s instructions
Thanks for this great article and all the comments. It took me a few hours to sort this out, but my work PC appears healthy again so I can go about making a living –
Andre, Jakiii and others, thanks for posting your methods of replacing the services file in such detail!
Thank you SO much for your work putting this together! So many websites have only the info on how to get rid of it, but yours was top-o-the-heap when it comes to undoing the damage that damn virus does. Well done, sir!
Many thanks for this article and the comments (in a pretty similar position to JJ at the moment, with a raid 0 array and no dual boot, so I used the SFC solution), because of this I was able to finally remove the sirefef.W problem and get my PC working once more. I’d still like to find out the extent to which this virus has messed up my registry, though…
Does this thing work on windows 7 32bit
Hi Rivo,
The registry exports should work same on a 32bit system. The service.exe that I included in the zip archive is from c:\windows\system32 so it should work on a 32bit system. To be 100% sure, you might want to find a copy from a Windows 7 32bit system or you can follow JJ’s excellent suggestion in comments to run “SFC /Scanfile=C:\Windows\System32\Services.exe” which will have Windows replace the file for you.
Hope that helps.
Thank you so much. You really saved me a lot of time.
Been fighting a loosing battle with a corrupt Services.EXE file for 24 hours. Found this article and downloaded your clean Services.EXE. Then used info found in this Microsoft KB http://support.microsoft.com/kb/929833 and the problem seems to be solved
Thank you for this guide ^^
@Chanh
Please add the tip from Anon2012 Combofix!
Combofix is a nice little programm which will remove the rest that comes along with this trojan!
How i removed this:
On my pc was Eset Internet Security which prevented some damage, but couldn’t do much
I then used ubuntu to replace the services.exe
Scanned my pc with malewarebytes antimalware
Ran offline scann with:
Kaspersky Rescue Disk 10 from USB Stick
then all the registry tricks from this guide and Combofix…
Up and runnig clean again!
thank you
Oh, I love ComboFix. It is my go-to tool for rootkit removal on Windows XP. Until recently it didn’t support Windows 7 64bit… though now I see that Windows 7 64bit is listed as supported. Cool. Next opportunity, I will try Combofix on Windows 7 64bit to see how it does.
Many thanks! I searched all day and only found the wscsvc reg fix. Spent all day trying to find fixes after I found the virus. I was fortunate enough to copy the reg files from another Win7 64 computer, followed your directions above and now all is well. Phew! Awesome site, I’ll keep you bookmarked. Thanks again!!!
Thank you for this. I too spent many hours working on this problem and your information was what I needed. FYI for others looking for help. I first had to remove ZeroAccess Trojan (many variants like .y, .u etc.) using HitmanPro. The other programs I tried (McAfee, SuperAntiSpyware, tdssKiller,Malwarebytes) would find the files, but not remove them.
Thanks so much for this! I had the ZeroAccess Trojan at work and between myself and our outside tech company it took us hours to get my work computer back up and running!! Turned on the home computer tonight and had a major virus that I was able to remove but your post above enabled me to get back all of my security settings in under an hour!! I’m forward this post along to our outside tech company to help someone else in the future. Thanks again!!
Thank you so much for this extremely useful guide as well as the clean services.exe file!
However, after following the instructions here I was only able to get BFE and Windows Firewall back up, but BITS and Windows Update services are still missing, even though I can see their entries in the registry just fine. Would you happen to have any clue on this? Maybe I should give you some background…
Mine was a bit of an unusual case, in that my laptop was working fine all along until about 3-4 days ago, when I noticed that MSE had been disabled. Didn’t take too much notice since everything seemed to be fine, until today I decided to look into the root cause, and holy crap I found that all security related services had been wiped (exactly as described in this article), and System Restore didn’t work anymore! I backed all my important data and then stumbled upon this article.
Update: Did another scan with MSE, and it picked up this thing called Win64/Necurs.A
When I tried removing it with MSE, it completely screwed up my system and Windows wouldn’t even boot! Luckily the startup recovery program kicked in and fixed the problem, but it seemed to have undone all my hard work! So this time, I went over to ESET’s website and downloaded their Sirefef removal tools. That fixed the icon rearranging problem, but I still couldn’t get BITS and Windows update to start.
Finally, after downloading and running the Win64/Necurs.A tool, both BITS and Windows Update have been restored.
Just thought I’d let people know in case someone runs into my situation as well.
Hi Richard,
Glad you managed to fix your system and thank you for sharing the information on how you did it. It looks like you were hit with two different viruses at the same time… bummer. I will try the ESET Sirefef removal tool to see if it will fix my icons rearranging issue.
Thanks again.
Thank you for writing this article. After countless hours of researching and trying to fix the problem without any luck, I was almost going to reinstall Windows. This is exactly what I needed!
Man I wish I would have found this before going through each service to find which one it cleaned out! Great work and a great post.
First of all, thanks much for this methodic, comprehensive article, plus the “fix” regkeys! Those and the full list of missing services is what I needed. I had variations of Sirefef – A,AB,B,P,W which also added other components listed below. I also have some other basic suggestions during any cleanup process.
– If you have a bootable system at least, and have an external drive or secondary internal drive, take a full backup of C:\ prior to cleaning and definitely when complete.
– Disable System Restore before cleanup, and then enable it again after fully cleaning PC – Sirefef was storing payload files in the System Volume Information file and disabling should flush those.
– I used a Ubuntu boot CD to access files and folders initially. It also allowed me to examine the SVI file and delete the Sirefef files there.
– Go to this site to get a DVD image for some variations of Windows 7, with or without SP1, to have a source for correct copies of files – read elsewhere on how to extract files from it with 7Zip.
– You can also use this DVD to; boot into Repair Mode/Command Prompt to replace and delete virus files, run a command line copy of Regedit, run Notepad to paste and save info, etc. The DVD does not prompt for a license key if used this way.
– If any clean steps produce a BSOD with a 5F stop code, run the full Repair mode from the Win7 Install DVD. Make sure to use the correct DVD for your WIN 7 version!
Additional places to check for Sirefef components – most will require booting with Ubuntu or Win7 Install CD or equivalent to delete files.
– The SVI file as mentioned – Ubuntu
– %windir%\system32\installer – check contents of each hex-value folder name to locate a sub-folder “U” with files like “@” in it. Delete the high level folder – save the key name. Ubuntu GUI easier than with Win7 DVD
– Search in the Registry for the name of the hex key value and delete it – Win7 Boot DVD, Repair mode, then start Regedit from command line
– Delete \%windir%\system32\assembly\GAC_32\Desktop.INI – just that file
– Delete \%windir%\system32\assembly\GAC_64\Desktop.INI – just that file
– Delete \%windir%\system32\services.exe00FE40…… or any variation that has a long hex value added to the name
Link for Win7 ISOs
http://techpp.com/2009/11/11/download-windows-7-iso-official-direct-download-links/
Great article, thanks!
Somewhat in addition to Andre’s comment: if you are (a) too lazy to use a bootdisk or rescuedisk or (b) don’t have a dual boot system and (c) Microsof Security Essentials reboots your computer due to services.exe being infected:
You have about one minute before the computer reboots and “shutdown -a” doesn’t help. But you have enough time to disable MSE’s realtime protection. Once you disable the realtime protection, the computer won’t restart automatically and you can delete services.exe (and copy a clean one).
Thanks a bunch for this clear explanation, can I give you $5?
Hi Austin,
Thanks for the offer. I’m doing okay so no need for donations. 🙂
Regards.
Chanh,
I spent an hour or so trying all the other fixes from MS blogs for my client’s computer that had been infected. I then backed up the registry and took the leap of faith and applied your registry patches.
Thank you, thank you, thank you!
Phil
Hi Chanh,
Another satisfied customer! Yours was by far the most comprehensive (and comprehensible) account of how to fix this nasty that I came across, and fix it it did. Thanks for it and for all the confirming comments, all of which contribute to one’s confidence that the fixes will work and are genuine.
Not a niggle, but if you do update the intructions again Number 6 needs sub-step 2 adding back in just like 3 above it since it is referred to in sub-step 1. I would reckon that nobody who got that far would be phased by this tiny omission.
Before applying your solution I had done a few permissions changes that included adding a user MpsSvc but without the ‘NT System\’ prefix that you recommend. So when I met an existing MpsSvc as I went through your steps I took the precaution of removing the old and adding in a new one with the prefix. I shall try to find out more about the significance of using the ‘NT System\’ prefix.
For me, the other great eye-opener of curing this infection is the use of Regedit exports from a healthy computer as Imports into the sick one. I should like to know more about when this technique is applicable and when it has to be used with care or perhaps only after editing the exported .reg file. I imagine that any references to the hardware and software configuration of the source machine might have to be excluded. I am probably displaying my ignorance of the workings of the registry by making the above remark.
The upside of having to deal with these annoying infections is that one comes away just that bit more confident about handling the next one. But this is dependent on finding a post as good as yours to help you on the way of enlightenment.
Thank you very much for your helpful post.
Hi SteveB,
Thanks for the correction for the missing step 6 substep 2. I’ve updated to the post to include the missing substep.
The registry export files are human readable. If you open it in a text editor, you can see that for services at least, it didn’t have anything too dependent on the hardware configuration. As for software, the Windows configuration that the export files refer to appear to be standardized.
Regards.
This is the best solution I have found for this problem. Very easy to follow and worked first time, I am very happy with this…
One more happy reader. I found other sites on this problem, but yours was the clearest, and the zip file with all the registry entries was exactly what I needed since I have no easy access to another Win7 computer.
After going thru all your steps, I got Windows Update and the other services back, but 3 files wouldn’t update. In addition, my system blue-screened every 50 minutes or so. sfc /scanfile didn’t find any corrupted files.
My next step was to download and run tdsskiller. It found a bad file and removed it. After rebooting, Norton then popped up with 3 more problems. After that, everything was fine, and my system is now running perfectly.
Hi all – A big thanks to Chanh, gvosden and everyone else who put this solution together.
Based on the info in this article and a bit of practical magic, I’ve put together an module for RES Automation Manager that can execute this workload unattended across many computers.
Check out the article on my site here:
http://resguru.com/2012/08/defeating-a-live-virus-trojan-infection-with-am/
Thanks again,
Max
Thank you so much! My computer intimidates me and I was all set to give up when I found this. Again, thank you.
Wonderfull post, indeed the best I’ve found after two days looking for a fix for the firewall problem. This is the only site with the fix complete and with a perfect explanation
Thanks, thanks, thanks
Fantastic job! Thanks so much!
Great scott!
Thank you so much for supplying reg fixes but most of a a good clean services.exe
+1 cookie for you
Thank you so much for this! Was having the damnedest time fixing the ravages of that nasty, nasty virus. You’re my hero!
Incredible. The work of a genius! I am thankful that people like you exist. Thank you very very much!
Thanks so much for your article. It fixed my bits problem without any fuss. None of the other sites were of any help. Great Job THANKS
ChanH – you sir (or madam) are a stud! After going down several blind alleys by searching on the MS error codes I lucked into your post above. It worked like a charm and everything is updating now. Thanks so much for the download and the easy to follow instructions.
Dude!! You flat out saved my butt! I see this darn virus so often, I have even been driven to formatting the box over it. From now on I am turning to your site first.
Thanks BIG HUGS,
Chris
I can not thank you enough for this reg fix I went from BSOD, to
Chckdsk from a dual boot, to the infected OS, and WIN repair disk to realizing that the services were deleted, I installed the reg entries, and windows Update works I dont rely on windows firewall so I dont want to see another error message unless I have to. I think my pc was hacked, I am not sure is it still vulnerable, I really dont want to flatten and re install Windows.. what do think ????
Hi G,
I’m glad your machine and Windows Update are working again. If you don’t wish to re-install, you can ensure that your computer is relatively safe by running several virus, spyware, and rootkit scanners. To start, I recommend running full scans using Microsoft Security Essentials and Malwarebytes Malware Scanner (both are free). If you want to be even more certain and are okay with stronger tools, try running ComboFix, GMER, and TDSSKiller (all are free). If you don’t mind buying a commercial product, try ESET NOD32; though you might use ESET for free by running their online scanner and/or downloading a trial version.
Good luck!
Thanks Chaah, I actually read more about how critical the BFE, services are, and did all the recommended tasks you outlined in the registry and it works without error, excellent experience for me, thanks for the help and response, just glad I had a dual boot system to back up my data and run the chckdsk tool from The Win 7 pro OS. I have a few of the utilities you mentioned TDSS. Malwarebytes, so They all report Good and the Windows security Appears stable.. That Bug was Mfer..
Peace
G
great guide, worked perfect. just wish i found it 3 hrs earlier =0p.
i used the offline Microsoft security essentials to remove the infections. it worked really well
Cool, Mat. I didn’t know about the offline Microsoft Security Essentials tool. For those interested, I think Microsoft calls it Windows Defender Offline (which is the previous name for Security Essentials) and basically you create a bootable CD/DVD/USB which you start your computer with. The other free Microsoft standalone virus scanning tool that I learned from the comments is the Microsoft Safety Scanner.
Great Post, this help me to solve the permission prob, also thanks for the .reg Files i missed many of them in my own reg.
If I try to start without services, and kill the service process, I still cant paste over the clean services file it does not allow me access to replace the services file. Is this a permissions problem or something?
Hi Hmmm,
Usually if you can’t overwrite services.exe, it means it is currently in use by Windows. Try following the instructions from JAKiii in the comments above to use msconfig to disable the services first before replacing services.exe. Alternatively, if you have a second machine, you can create a bootable CD containing Windows Defender Offline which you boot the infected machine from.
Regards.
I just wanted to comment, since I’m using Windows 7 HP without SP1. If you want to update this in your post above, it would be quite helpful actually, for those who are in the same situation as me.
For those who don’t have SP1, I’ve uploaded services.exe for my non-SP1 Home Premium below.
http://www.mediafire.com/?4k1aofh74wpu4zu
Of course, if you think I’m posting a virus or something, you’re free to extract the original services.exe from your Windows 7 disk yourself, with the instructions below:
http://www.sevenforums.com/tutorials/42776-extract-files-windows-7-installation-dvd.html
Hi John,
Thanks for posting your non-SP1 services.exe and the instructions on how to extract from the Windows install DVD. I’ve added a note to the blog text to refer to your comment for those who don’t have Service Pack 1 (SP1). I also recommended that anything downloaded, including my own posted zip file, be scanned by a virus scanner before using. I learned this lesson many years ago after my best friend gave me a virus even though he swore the disk was clean.
I do recommend that once folks get their machine working, that they upgrade to SP1. I believe the later Microsoft security updates require SP1 and won’t install otherwise.
Regards.
@Chanh: Yep, no problem. If it means anything, I’m on 64-bit, if the services.exe is dependent upon x86 or x64. I don’t think so though.
For the most part, I had to fix Sirefef myself a while ago as I couldn’t find a good enough guide on Google, but I essentially just used the dual-boot method to replace my services.exe with a clean one.
After I incidentally came upon this one after trying to figure out why my Windows Update wasn’t working, I figured I’d just help out a bit.
On a side note, I didn’t need to remake any permissions for the services or anything; I just needed to apply the registry fixes and a simple restart worked. Updates actually came right after the restart. I guess it could be case-by-case.
Peace out!
Booted into safe mode, ran the fixes, renamed the old services.exe to services._xe copied the services.exe from the zip to the system32 folder and rebooted the PC. All now appears to be working again as normal. Thank you
10x very much it was really helpfull
@Andre and @Jakii, I had no clue and resorted to the internet when my services.exe was corrupted. System restore did not work. Then I followed the steps you mentioned.
Only difference is Windows 7 takes time to copy/delete the services.exe and you have to do it before system restart. So, I used the command prompt to replace the services.exe.
After that, 38 updates were installed on my machine and its working perfectly. Thanks a ton!!
April 1 2013
I must thank you for this. I had exactly the same problem (from the same virus). Your work enabled me to fix it. I wish I had found it sooner, but I had not established the connection with the virus – I just seemed to have a number of unconnected problems.
[…] Recover From The "win64/Sirefef.W" Virus Infection https://www.chanhvuong.com/1259/recover-from-the-sirefef-y-virus-infection/ […]
Hi Chanh,
Many many many many thanks for this, spend almost a day at several microsoft support pages until i found your crystal clear step by step plan resulting in successful pass!
BIG THANKS!!!